Uncategorized
Unlocking the Cyber Trends: A Deep Dive into Trendzguruji.me
Published
10 months agoon
By
admin
In the fast-paced digital landscape of today, staying updated with the latest cyber trends is essential for individuals and businesses alike. One platform that has been making waves in the cybersecurity world is Trendzguruji.me. In this article, we will explore what Trendzguruji.me is all about, its significance in the cyber realm, and how it can benefit you. Let’s embark on this cyber journey together!
Table of Contents
- Introduction to Trendzguruji.me
- The Evolution of Cybersecurity
- Trendzguruji.me: A Beacon of Knowledge
- Navigating the Platform
- User-Friendly Interface
- Categories and Topics
- Interactive Forums
- In-Depth Cyber Insights
- Tutorials and Guides
- Cyber Threat Analysis
- Emerging Technologies
- Community Engagement
- Discussion Boards
- Networking Opportunities
- Staying Ahead of the Curve
- Real-time Updates
- Customized Notifications
- Security and Privacy
- Data Protection
- Safe Browsing Practices
- The Power of Collaboration
- Contributor Programs
- Peer Learning
- The Global Impact
- International Users
- Cross-Cultural Exchange
- Case Studies and Success Stories
- Benefits for Businesses
- Challenges and Concerns
- Future Prospects
- Conclusion: Embracing Trendzguruji.me
Introduction to Trendzguruji.me
Trendzguruji.me is not just another website; it’s a knowledge hub for all things related to cybersecurity. Founded by a group of passionate cybersecurity experts, this platform aims to educate, inform, and connect individuals and businesses in the ever-evolving world of cyber threats.
The Evolution of Cybersecurity
In recent years, the cybersecurity landscape has undergone significant changes. With the rise of digitalization and remote work, the need for robust cybersecurity measures has become more critical than ever. Trendzguruji.me was born out of this necessity, providing a platform where both beginners and experts can gather to enhance their cybersecurity knowledge.
Trendzguruji.me: A Beacon of Knowledge

One of the standout features of Trendzguruji.me is its commitment to knowledge dissemination. The platform offers a vast repository of articles, tutorials, and guides on a wide range of cybersecurity topics. Whether you’re interested in learning about encryption, malware detection, or ethical hacking, you’ll find valuable resources here.
Navigating the Platform
User-Friendly Interface
Trendzguruji.me prides itself on its user-friendly interface. Navigating the website is a breeze, even for those with limited technical knowledge. The intuitive design ensures that you can find the information you need quickly and efficiently.
Categories and Topics
The platform covers a broad spectrum of cybersecurity categories and topics. From basic cybersecurity practices to advanced threat analysis, Trendzguruji.me has it all. You can explore different categories to find content that suits your interests and needs.
Interactive Forums
Trendzguruji.me encourages community engagement through its interactive forums. Here, you can connect with like-minded individuals, ask questions, and share your insights. It’s a place where the cybersecurity community comes together to learn and grow.
In-Depth Cyber Insights
Tutorials and Guides
One of the highlights of Trendzguruji.me is its collection of detailed tutorials and guides. These step-by-step resources empower users to enhance their cybersecurity skills. Whether you’re a novice or an experienced professional, you’ll find valuable information to level up your cybersecurity game.
Cyber Threat Analysis
Stay informed about the latest cyber threats with Trendzguruji.me’s comprehensive threat analysis. The platform provides real-time updates on emerging threats, helping you stay one step ahead of cybercriminals.
Emerging Technologies
The world of cybersecurity is constantly evolving. Trendzguruji.me keeps you updated on the latest trends and emerging technologies in the field. From AI-driven security solutions to blockchain advancements, you’ll find insights into the future of cybersecurity.
Community Engagement
Discussion Boards
Engage in meaningful discussions with cybersecurity enthusiasts from around the world. Trendzguruji.me’s discussion boards are a place where ideas are exchanged, problems are solved, and connections are made.
Networking Opportunities
The platform also offers networking opportunities for professionals looking to expand their horizons. Connect with cybersecurity experts, potential collaborators, and mentors who can guide you on your cybersecurity journey.
Staying Ahead of the Curve

Real-time Updates
Cyber threats evolve rapidly. Trendzguruji.me ensures that you receive real-time updates on the latest developments in the cybersecurity landscape. Stay informed to protect your digital assets effectively.
Customized Notifications
Tailor your Trendzguruji.me experience with customized notifications. Receive alerts about topics that matter most to you, ensuring that you never miss out on critical information.
Security and Privacy
Data Protection
Trendzguruji.me takes your privacy seriously. The platform employs robust data protection measures to safeguard your personal information. You can browse and learn without worrying about your data falling into the wrong hands.
Safe Browsing Practices
In addition to teaching you about cybersecurity, Trendzguruji.me promotes safe browsing practices. Learn how to protect yourself from online threats and make the internet a safer place for everyone.
The Power of Collaboration
Contributor Programs
Trendzguruji.me welcomes contributions from cybersecurity enthusiasts worldwide. Share your knowledge and expertise by becoming a contributor. Contribute to the community’s growth while establishing yourself as a trusted cybersecurity voice.
Peer Learning
The platform’s peer learning environment fosters collaboration and knowledge sharing. Learn from your peers, exchange ideas, and collectively raise the bar for cybersecurity awareness.
The Global Impact
International Users
Trendzguruji.me boasts a diverse user base with members from across the globe. This international perspective enriches the platform, providing insights into cybersecurity challenges and solutions from different cultural perspectives.
Cross-Cultural Exchange
Engage in cross-cultural exchanges with cybersecurity professionals and enthusiasts. Gain a broader understanding of global cybersecurity trends and practices.
Case Studies and Success Stories

Explore real-world case studies and success stories on Trendzguruji.me. Learn how businesses and individuals have overcome cyber challenges with the help of the platform’s resources and community support.
Benefits for Businesses
Discover how Trendzguruji.me can benefit businesses of all sizes. From improving cybersecurity measures to fostering employee awareness, businesses can leverage the platform to protect their digital assets effectively.
Challenges and Concerns
While Trendzguruji.me offers a wealth of resources, it’s essential to acknowledge the challenges and concerns in the cybersecurity landscape. Stay informed about potential threats and vulnerabilities to stay prepared.
Future Prospects
As the cybersecurity landscape continues to evolve, Trendzguruji.me remains committed to being a trusted source of knowledge. Explore the platform’s future plans and how they aim to stay at the forefront of cybersecurity education.
Conclusion: Embracing Trendzguruji.me
In conclusion, Trendzguruji.me is more than just a website; it’s a community, a resource, and a beacon of knowledge in the world of cybersecurity. By engaging with this platform, you can stay informed, connect with experts, and enhance your cybersecurity skills. Embrace the cyber trends with Trendzguruji.me and take your digital security to the next level.
FAQs
- Is Trendzguruji.me suitable for beginners in cybersecurity?
- Absolutely! Trendzguruji.me offers resources for all skill levels, including beginners.
- Are there any membership fees for using Trendzguruji.me?
- No, Trendzguruji.me is a free platform for all users.
- How can I contribute to Trendzguruji.me as a cybersecurity expert?
- You can join the contributor program and share your knowledge with the community.
- Is my data safe on Trendzguruji.me?
- Yes, Trendzguruji.me prioritizes data protection and implements strict security measures.
- What is the future vision of Trendzguruji.me in the cybersecurity landscape?
- Trendzguruji.me aims to continue evolving and providing up-to-date cybersecurity resources for its users.
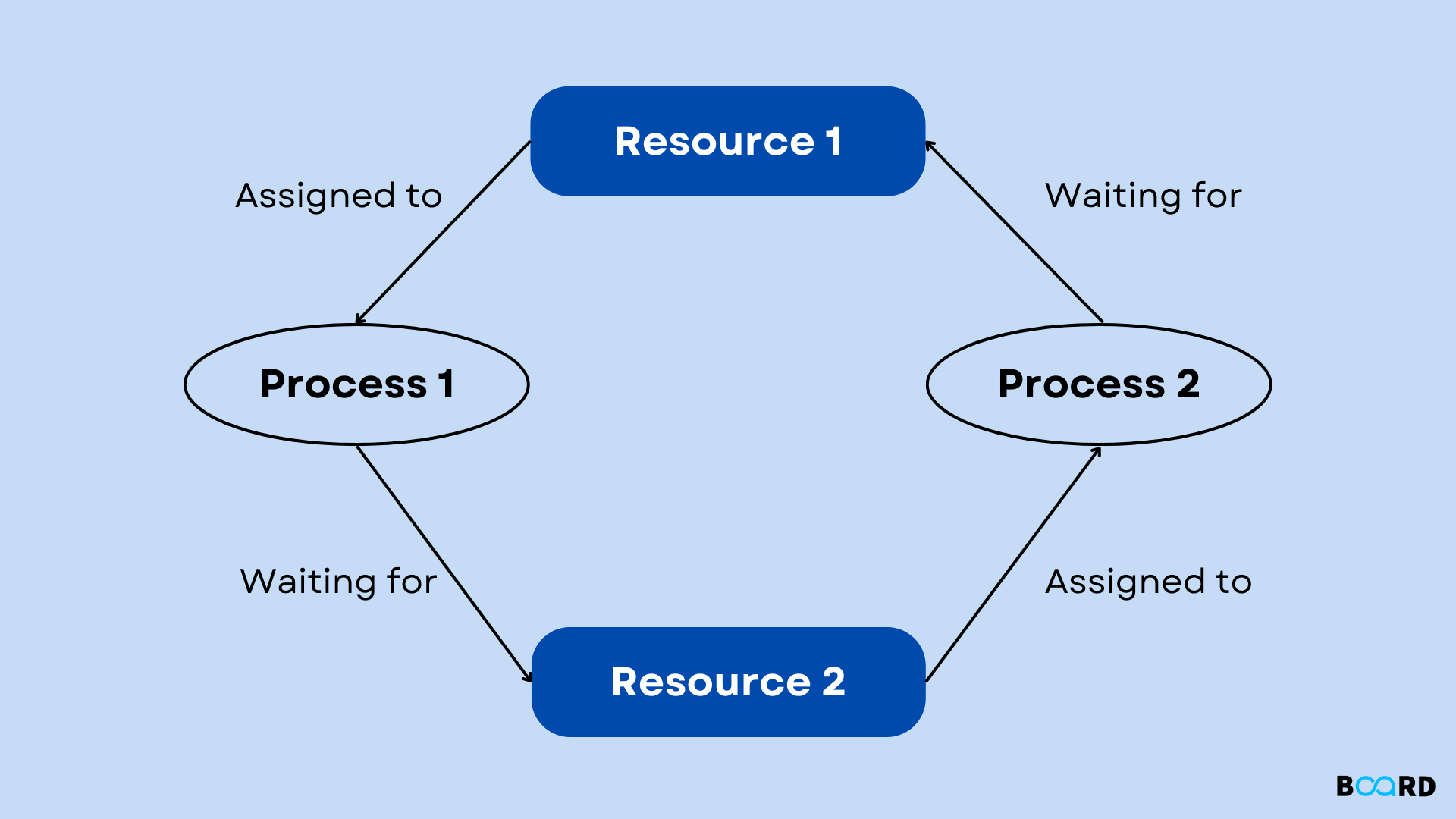
Deadlock is a common phenomenon in database management systems (DBMS) that occurs when two or more transactions are unable to proceed because each is waiting for the other to release resources. Understanding deadlock is crucial for database administrators and developers to ensure the smooth operation of their systems.
In the realm of Database Management Systems (DBMS), deadlocks are a significant concern that can impede the performance and functionality of systems. To delve into this topic comprehensively, we’ll explore what deadlocks are, how they occur, their impact on DBMS, strategies for detection and prevention, and practical examples to grasp their real-world implications.
What is a Deadlock?
A deadlock in DBMS occurs when two or more transactions are waiting indefinitely for a resource held by each other, resulting in a standstill. Imagine a scenario where Transaction A holds Resource X and needs Resource Y, while Transaction B holds Resource Y and needs Resource X. This circular dependency leads to a deadlock situation where neither transaction can proceed.
Causes of Deadlocks
Understanding the root causes of deadlocks is crucial for effective management. Deadlocks typically arise due to four conditions known as the Coffman conditions:
- Mutual Exclusion: Resources cannot be shared; only one transaction can use a resource at a time.
- Hold and Wait: Transactions hold resources while waiting for others, creating potential for deadlock.
- No Preemption: Resources cannot be forcibly taken from transactions; they must be released voluntarily.
- Circular Wait: A circular chain of transactions exists, each waiting for a resource held by the next.
Conditions for Deadlock
Mutual Exclusion
Deadlock arises due to the principle of mutual exclusion, where only one process can access a resource at a time. If one transaction holds a resource and another transaction requests the same resource, deadlock can occur.
Hold and Wait
Transactions in a deadlock situation hold resources while waiting for additional resources to be allocated. This can lead to a scenario where each transaction is waiting for a resource held by another, resulting in a deadlock.
No Preemption
In deadlock, resources cannot be forcibly taken away from transactions that are currently holding them. This lack of preemption contributes to the deadlock condition.
Circular Wait
A circular wait occurs when two or more transactions are waiting for resources that are held by each other in a circular chain. This circular dependency prevents any of the transactions from progressing, leading to deadlock.
Impact on DBMS
Deadlocks can have severe consequences in a DBMS environment, including:
- System Hang: Transactions are unable to proceed, leading to system deadlock and unresponsiveness.
- Resource Wastage: Locked resources are unavailable to other transactions, causing inefficiency.
- Data Integrity Risks: Incomplete transactions due to deadlock can compromise database integrity.
Detection and Prevention Strategies
DBMS employs various techniques to detect and prevent deadlocks:
Detection:
- Deadlock Detection Algorithms: Algorithms like the wait-for graph can identify deadlock situations.
- Timeouts: Setting timeouts for transactions can help detect and abort those stuck in deadlock.
Prevention:
- Locking Protocols: Implementing locking protocols like two-phase locking can prevent circular wait conditions.
- Deadlock Avoidance: Predicting potential deadlocks and preventing them by careful resource allocation.
Preventing deadlock involves implementing strategies to ensure that the conditions necessary for deadlock cannot occur.
Resource Allocation Strategies
By carefully managing resource allocation, it’s possible to prevent deadlock. This can involve ensuring that transactions request all the resources they need at the beginning or releasing resources before requesting new ones.
Avoiding Hold and Wait
One approach to prevent deadlock is to require transactions to request all the resources they need simultaneously. This eliminates the possibility of a transaction holding resources while waiting for others.
Introducing Preemption
Preemption involves forcibly removing resources from transactions to resolve deadlock situations. While effective, preemption can be complex to implement and may impact system performance.
Breaking Circular Wait
By restructuring the way resources are allocated or limiting the number of resources a transaction can hold simultaneously, it’s possible to break circular wait scenarios and prevent deadlock.
Practical Examples
Consider a banking system where one transaction transfers funds from Account A to Account B while another transaction transfers funds from Account B to Account A. If both transactions lock their respective accounts before proceeding, a deadlock can occur if they attempt to lock the second account before releasing the first.
Deadlock Avoidance
In addition to prevention strategies, deadlock avoidance techniques aim to dynamically allocate resources in a way that avoids deadlock.
Banker’s Algorithm
The Banker’s algorithm is a deadlock avoidance technique that analyzes resource allocation requests to ensure that granting them won’t lead to deadlock. This involves simulating resource allocation scenarios to determine if they are safe.
Resource Allocation Graph
A resource allocation graph is another method for deadlock avoidance, where transactions are represented as nodes and resource allocation requests are represented as edges. By analyzing the graph, it’s possible to detect and prevent potential deadlock situations.
Deadlock Detection
Despite prevention and avoidance efforts, deadlock may still occur. In such cases, it’s important to have mechanisms in place to detect and resolve deadlock situations.
Techniques for Detecting Deadlock
Various algorithms and techniques exist for detecting deadlock, such as the wait-for graph algorithm or the timeout-based approach. These techniques periodically check for deadlock conditions and take appropriate action if detected.
Recovery from Deadlock
Once deadlock is detected, recovery strategies are employed to resolve the situation. This can involve aborting transactions, rolling back changes, or forcibly releasing resources to break the deadlock.
Comparison of Prevention, Avoidance, and Detection
Each approach to dealing with deadlock has its own set of advantages and disadvantages. Prevention strategies are proactive but may be restrictive, avoidance techniques are more flexible but require additional overhead, and detection methods incur computational costs but can effectively handle deadlock situations as they arise.
Real-world Examples of Deadlock
Deadlock isn’t just a theoretical concept; it can occur in real-world systems with serious consequences. Instances of deadlock in computer systems, such as database servers or operating systems, can lead to system crashes, data corruption, or loss of service.
Tips for Dealing with Deadlock
To minimize the occurrence of deadlock and mitigate its impact, it’s important to follow best practices. This includes properly managing resource allocation, designing robust transaction protocols, and implementing effective deadlock detection and recovery mechanisms.
Conclusion
Deadlock is a significant challenge in database management systems, but with the right strategies and techniques, it can be effectively managed. By understanding the conditions that lead to deadlock and implementing appropriate prevention, avoidance, and detection methods, database administrators can ensure the reliability and performance of their systems.
Unique FAQs
- What is the difference between deadlock prevention and deadlock avoidance?
- Deadlock prevention focuses on eliminating the conditions necessary for deadlock to occur, while deadlock avoidance aims to dynamically allocate resources in a way that avoids deadlock situations altogether.
- How does the Banker’s algorithm work in deadlock avoidance?
- The Banker’s algorithm analyzes resource allocation requests to ensure that granting them won’t lead to deadlock. It simulates resource allocation scenarios to determine if they are safe before granting resources to transactions.
- Can deadlock occur in single-user systems?
- While less common, deadlock can still occur in single-user systems, particularly in scenarios where multiple processes or threads are involved and compete for resources.
- What are some common symptoms of deadlock in a database system?
- Symptoms of deadlock may include unresponsive transactions, stalled processes, or system-wide performance degradation due to resource contention.
- How can database administrators proactively monitor and prevent deadlock?
- Database administrators can implement monitoring tools to detect deadlock conditions early, analyze system logs for signs of resource contention, and regularly review transaction protocols and resource allocation strategies to identify potential deadlock risks.
Uncategorized
Unlocking Entertainment: Understanding hbomax/tvsignin enter code-In Enter Code
Published
5 months agoon
February 29, 2024By
admin
In the digital age, entertainment has become synonymous with streaming services. From binge-worthy series to blockbuster movies, these platforms offer a vast array of content at our fingertips. HBO Max stands out as a premier destination for streaming, boasting a library of acclaimed shows, exclusive movies, and original programming. However, accessing this treasure trove of entertainment often requires navigating through various sign-in processes, including the infamous “TV Sign-In Enter Code” prompt. In this comprehensive guide, we delve into the intricacies of HBO Max, decipher the TV sign-in procedure, and provide invaluable insights into maximizing your streaming experience.
Unveiling HBO Max: A Universe of Entertainment
Launched in May 2020, HBO Max emerged as a formidable contender in the streaming wars. Backed by WarnerMedia, this platform combines the vast content library of HBO with an extensive selection of Warner Bros. films, classic TV shows, exclusive originals, and licensed content. From timeless classics like “Game of Thrones” to contemporary hits like “Succession,” HBO Max caters to a diverse audience with varied tastes.
The Sign-In Conundrum: Deciphering TV Sign-In Enter Code
While accessing HBO Max on a computer or mobile device is straightforward, the process becomes slightly more complex when utilizing a smart TV or streaming device. Users often encounter the “TV Sign-In Enter Code” prompt, prompting them to authenticate their HBO Max account on their chosen device. But what exactly does this entail?
Step 1: Launch HBO Max on Your Device
Begin by navigating to the HBO Max app on your smart TV or streaming device. If you haven’t installed the app yet, head to the app store or channel store and download HBO Max.
Step 2: Select “Sign In”
Once the app is launched, locate the option to sign in. This is usually found on the home screen or in the app’s settings menu. Select “Sign In” to proceed.
Step 3: Obtain the Activation Code
At this stage, the app will display an activation code on your TV screen. This code is unique to your device and serves as a one-time authentication token.
Step 4: Visit the HBO Max Activation Website
Using a web browser on your computer or mobile device, navigate to the HBO Max activation website. This is typically hbomax.com/tvsignin or a similar URL provided by HBO Max.
Step 5: Enter the Activation Code
On the activation website, you’ll be prompted to enter the activation code displayed on your TV screen. Ensure accuracy when inputting the code to prevent any errors.
Step 6: Sign In to Your HBO Max Account
After entering the activation code, you’ll be directed to sign in to your HBO Max account. Enter your credentials (email address and password) associated with your HBO Max subscription.
Step 7: Success!
Once you’ve successfully signed in, your smart TV or streaming device will be authenticated, granting you access to the full catalog of HBO Max content.
Troubleshooting Tips: Overcoming Common Challenges
While the TV sign-in process is relatively straightforward, users may encounter occasional issues or obstacles. Here are some troubleshooting tips to address common challenges:
Issue: Activation Code Expired
If the activation code displayed on your TV screen has expired, simply refresh the screen to generate a new code. Alternatively, navigate back to the sign-in menu on the HBO Max app to generate a fresh code.
Issue: Incorrect Activation Code
Ensure that you’re entering the activation code accurately, taking care to distinguish between similar-looking characters (e.g., “O” and “0,” “I” and “1”). If the code still doesn’t work, try refreshing the screen to generate a new code.
Issue: Account Authentication Failure
If you’re experiencing difficulties signing in to your HBO Max account, double-check your credentials to ensure they’re entered correctly. If you’ve forgotten your password, utilize the “Forgot Password” feature to reset it.
Issue: Device Compatibility
Not all smart TVs and streaming devices are compatible with HBO Max. Before attempting to sign in, verify that your device is supported by checking HBO Max’s official website for a list of compatible devices.
Maximizing Your HBO Max Experience: Tips and Tricks
Now that you’ve successfully signed in to HBO Max on your preferred device, it’s time to make the most of your streaming experience. Here are some tips and tricks to enhance your HBO Max journey:
Create Customized Profiles
Take advantage of HBO Max’s profile feature to personalize your streaming experience. Create separate profiles for family members or roommates to ensure personalized recommendations and watchlists.
Explore Curated Collections
HBO Max offers a plethora of curated collections catering to various interests and genres. Whether you’re a fan of documentaries, comedies, or international cinema, there’s a collection tailored to your preferences.
Utilize Downloadable Content
For on-the-go viewing or times when an internet connection is unavailable, HBO Max allows users to download select titles for offline viewing. Simply download your favorite shows or movies to your device and enjoy them anytime, anywhere.
Stay Updated with New Releases
Keep abreast of the latest additions to the HBO Max library by regularly checking the “New Releases” section. From blockbuster premieres to critically acclaimed originals, there’s always something new to discover on HBO Max.
Engage with Community Features
HBO Max offers community features such as discussion boards and watch parties, allowing users to engage with fellow fans and share their thoughts on favorite shows and movies.
Conclusion: Unlocking the Gateway to Premium Entertainment
In a landscape inundated with streaming options, HBO Max stands out as a beacon of quality entertainment. By understanding the intricacies of the TV sign-in enter code process and implementing the provided tips and tricks, users can unlock the full potential of HBO Max and immerse themselves in a world of captivating content. Whether indulging in a binge-watching marathon or discovering hidden gems, HBO Max offers something for everyone, revolutionizing the way we consume entertainment in the digital age. So, grab your remote, enter that code, and embark on an unforgettable streaming journey with HBO Max.
Uncategorized
Unveiling the Secrets to a Handsome Life: A Comprehensive Guide
Published
6 months agoon
January 20, 2024By
admin
In a world filled with endless possibilities, achieving a handsome life is a pursuit many strive for. But what does it truly mean to lead a life that exudes charm, vitality, and fulfillment? In this comprehensive guide, we’ll explore the various facets that contribute to a life that not only looks good on the surface but also feels good from within.
Embracing Physical Fitness for a Handsome You
A handsome life starts with a healthy and fit body. Regular exercise is the cornerstone of physical well-being. Incorporating a mix of cardiovascular exercises, strength training, and flexibility routines can significantly enhance your overall health. Remember, a handsome physique is not just about appearance; it’s about feeling strong, energetic, and confident.
Nourishing Your Body: The Foundation of Handsome Living
To truly radiate vitality, pay attention to what you eat. A well-balanced and nutritious diet is key to maintaining optimal health and achieving a handsome glow. Include a variety of fruits, vegetables, lean proteins, and whole grains in your daily meals. Hydration is equally crucial, so don’t forget to drink plenty of water to keep your skin and body hydrated.
Cultivating a Handsome Mind: The Power of Mental Wellness
A handsome life is not solely about physical well-being; mental wellness plays a pivotal role. Practice mindfulness through activities like meditation and deep breathing to alleviate stress and foster a positive mindset. A healthy mind contributes to enhanced decision-making, increased creativity, and an overall sense of well-being.
Dressing for Success: The Art of Handsome Fashion
Your appearance speaks volumes about your confidence and self-esteem. Dressing well is a crucial aspect of leading a handsome life. Invest in a versatile wardrobe that reflects your personal style and makes you feel good. Remember, it’s not about following trends blindly but about embracing a style that resonates with your personality.
Building Meaningful Connections: The Social Aspect of Handsome Living
A handsome life is enriched by the quality of relationships we cultivate. Nurture meaningful connections with friends, family, and colleagues. Surround yourself with positive influences, as social interactions contribute significantly to our overall well-being. Engage in activities that bring joy and fulfillment, creating a robust support system.
The Financial Canvas of a Handsome Life
Financial stability is a crucial component of a handsome life. Create a budget, save wisely, and invest in your future. Achieving financial goals not only provides a sense of security but also opens doors to opportunities that contribute to a more fulfilling life.
Exploring Passion and Purpose: The Soulful Essence of Handsome Living
To lead a truly handsome life, discover and pursue your passions. Engaging in activities that bring you joy and fulfillment adds a deeper layer to your overall well-being. Whether it’s a hobby, a career path, or a volunteer opportunity, align your life with your passions for a more satisfying existence.
Balancing Act: Time Management for a Handsome Lifestyle
Time is a precious commodity, and managing it effectively is vital for a handsome life. Prioritize tasks, set realistic goals, and create a schedule that allows for work, relaxation, and personal pursuits. A balanced lifestyle contributes to reduced stress levels and a more fulfilling existence.
Embracing Change: The Dynamic Nature of a Handsome Life
A handsome life is not static; it evolves with time. Embrace change, be open to new experiences, and continuously seek personal growth. Flexibility and adaptability are key traits that contribute to a life that remains vibrant and attractive.
Sustaining a Handsome Environment: Your Personal Sanctuary
Your living space is a reflection of your inner self. Create a handsome environment by decluttering, organizing, and personalizing your space. A clean and aesthetically pleasing environment contributes to a positive mindset and a more enjoyable lifestyle.
Conclusion: A Handsome Life Awaits You
In conclusion, the pursuit of a handsome life involves a holistic approach that encompasses physical health, mental well-being, meaningful relationships, financial stability, and personal fulfillment. By consciously integrating these elements into your life, you’ll not only look good but also feel good, creating a life that is truly handsome in every sense of the word. Embrace the journey, make intentional choices, and watch as your life transforms into a masterpiece of vitality and charm.

India National Cricket Team vs South Africa National Cricket Team Match Scorecard: A Detailed Analysis

8 Key Reasons To Choose Managed IT Services

The Irresistible Rise of Pizza Edition Games: A Delicious Journey through Gaming

Get your Canadian visa in a jiffy – Hong Kong citizens can now apply online!
BiharMasti: The Place to Download Bhojpuri Movies and Music

What states have no chase law for motorcycles
Trending
-

 Business2 years ago
Business2 years agoGet your Canadian visa in a jiffy – Hong Kong citizens can now apply online!
-
 Tips & Tricks2 years ago
Tips & Tricks2 years agoBiharMasti: The Place to Download Bhojpuri Movies and Music
-

 Law2 years ago
Law2 years agoWhat states have no chase law for motorcycles
-

 Technology2 years ago
Technology2 years agoHow to do Jio Prepaid Recharge Online
-

 Business2 years ago
Business2 years agoHow do MEP Services help contractors?
-

 Business1 year ago
Business1 year agoEverything You Need to Know About SQM Club
-

 Lifestyle2 years ago
Lifestyle2 years agoWhat is a lifestyle party? Few tips for hosting a lifestyle party
-
 Technology2 years ago
Technology2 years agoHow to Download Punjabi Movie Chhalla Mud Ke Nahi Aaya?



