Tech
History Of Gathering Hypothesis
Published
2 years agoon

The historical backdrop of gathering hypothesis, a numerical space that reviews bunches in their different structures, has created in different equal strings. Bunch hypothesis has three verifiable roots: the hypothesis of arithmetical conditions, number hypothesis, and geometry. Lagrange, Abel and Galois were early specialists in the field of gathering hypothesis.
Click here https://caresclub.com/
The earliest investigation of such gatherings presumably returns to crafted by Lagrange in the late eighteenth hundred years. Be that as it may, this work was to some degree unique, and the 1846 distributions of Cauchy and Galois are generally alluded to as the starting points of gathering hypothesis. The hypothesis didn’t foster in a vacuum, and in this manner 3 significant sutras in its pre-history are created here.
A principal foundation of gathering hypothesis was the quest for answers for polynomial conditions of degree more prominent than 4.
You can get some more knowledge 10 of 120
The issue of building a condition of degree m as its underlying foundations as the foundations of a given condition of degree n>m has an initial source. For basic cases the issue returns to Hoode (1659). Saundersson (1740) noticed that the assurance of the quadratic elements of a quadratic articulation definitely prompts a sextic condition, and Le Sharp (1748) and Waring (1762 to 1782) further explained on the thought. .
An overall reason for the hypothesis of conditions in view of a bunch of changes was tracked down by the mathematician Lagrange (1770, 1771), and the guideline of replacement was based on it. He found that the underlying foundations of all the resolvants (resolvents, reduits) he analyzed are normal elements of the foundations of the separate conditions. To concentrate on the properties of these capabilities he concocted a math des blends. The contemporary work of Vandermonde (1770) additionally foreshadowed the hypothesis to come.
Ruffini (1799) endeavored to demonstrate the difficulty of addressing quintic and higher conditions. Ruffini separated what is currently called intransitive and transitive, and loose and crude gatherings, and (1801) utilizes a gathering of conditions under the name l’assime delle permutazioni. He likewise distributed a letter from Abbati himself, in which the gathering’s perspective is noticeable.
Galois age fifteen, outlined by a colleague.
Galois saw that as if r1, r2, … rn a condition has n roots, then, at that point, there is consistently a bunch of changes of r with the end goal that
* each capability of invariant roots is known sensibly by substituent of the gathering, and
* Conversely, every sensibly resolved capability of the roots is irreversible under bunch substituents.
In present day terms, the feasibility of the Galois bunch related with the situation decides the resolvability of the situation with the extremist. Galois additionally added to the hypothesis of measured conditions and the hypothesis of elliptic capabilities. His most memorable distribution on bunch hypothesis was made at the age of eighteen (1829), yet his commitments got little consideration until the distribution of his Gathered Papers in 1846 (Liouville, vol. XI). Galois is worshipped as the primary mathematician to join bunch hypothesis and field hypothesis, with a hypothesis presently known as Galois hypothesis.
Bunches like Galois bunches are (today) called change gatherings, an idea strikingly explored by Cauchy. There are a few significant hypotheses in basic gathering hypothesis in light of Cauchy. Cayley’s gathering hypothesis, as it relies upon the representative condition n = 1 (1854), gives the main unique meanings of limited gatherings.
Second, the deliberate utilization of gatherings in math, for the most part assuming some pretense of evenness gatherings, was presented by Klein’s 1872 Erlangen program. [6] The investigation of what is presently called the Lai bunch started methodicallly with Sophus Lai in 1884, trailed by crafted by Killing, Study, Schur, Maurer and Container. Discrete (discrete gathering) hypothesis was instituted by Felix Klein, Lai, Poincaré and Charles mile Picard, particularly with respect to measured structures and monodromy.
The third base of gathering hypothesis was number hypothesis. Some abelian bunch structures were utilized by Gauss in number-hypothetical work, and all the more expressly by Kronecker. [7] Early endeavors to demonstrate Fermat’s last hypothesis were reached to a peak by Kummer, including bunches depicting duplication in indivisible numbers.
Bunch hypothesis as an undeniably free subject was promoted by Seurat, who committed Volume IV of his Polynomial math to the hypothesis; by Camille Jordan, whose Trate des replacements and des condition algebras (1870) is a work of art; and for Eugen Neto (1882), whose Hypothesis of Replacements and Its Applications to Polynomial math was converted into English by Cole (1892). Other gathering scholars of the nineteenth century were Bertrand, Charles Loner, Frobenius, Leopold Kronecker and Emil Mathieu; as well as Burnside, Dixon, Holder, Moore, Storehouse and Weber.
The combination of the over three sources into a typical hypothesis started with Jordan’s Traite and von Dyck (1882) who originally characterized a gathering in F.All present day implications. Weber and Burnside’s course readings laid out bunch hypothesis as a subject. [9] The theoretical gathering detailing didn’t matter to an enormous piece of nineteenth century bunch hypothesis, and an elective formalism was given with regards to Lie algebras.
In the period 1870-1900 the gatherings were portrayed as Untruth’s consistent gathering, irregular gathering, limited gathering of substituent roots (called steady stages), and limited gathering of direct replacement (typically of limited fields). went. During the period 1880-1920, the gatherings portrayed by creations showed signs of life of their own through crafted by Kelly, von Dyck, Dahn, Nielsen, Schreier and went on in the period 1920-1940 with crafted by Coxeter, Magnus and . Others to shape the field of combinatorial gathering hypothesis.
The period 1870-1900 saw features, for example, the Sylow hypothesis, Holder’s arrangement of gatherings of sans class request, and the early presentation of Frobenius’ personality hypothesis. Currently by 1860, gatherings of automorphisms of limited projective planes were considered (by Matthew), and during the 1870s Felix Klein’s gathering hypothetical vision was being acknowledged in his Erlangen program. Automorphism gatherings of higher layered projective spaces were concentrated by Jordan in his Trate and included piece series for the majority of the purported traditional gatherings, in spite of the fact that he kept away from non-prime fields and precluded unitary gatherings. The review was gone on by Moore and Burnside, and was brought to a thorough course book structure by Dixon in 1901. The job of straightforward gatherings was underlined by Jordan, and rules for nonlinearity were created by Holder until he had the option to arrange less basic gatherings of the request. more than 200. The review was gone on by F.N. Cole (until 660) and Burnside (until 1092), lastly by Mill operator and Ling in 1900 until 2001 toward the start of the “Thousand years Undertaking”.
Constant gatherings grew quickly in the period 1870-1900. Killing and Falsehood’s primary papers were distributed, Hilbert’s hypothesis invariant hypothesis 1882, and so forth.
In the period 1900-1940, endless “spasmodic” (presently called discrete gatherings) bunches ended their lives. Burnside’s popular issue prompted the investigation of erratic subgroups of limited layered direct gatherings over inconsistent fields and for sure erratic gatherings. Crucial gatherings and reflection bunches supported the advancement of J. A. Todd and Coxeter, like the Todd-Coxeter calculation in combinatorial gathering hypothesis. Mathematical gatherings characterized as answers for polynomial conditions (as opposed to following up on them, as in the earlier 100 years), benefited hugely from Falsehood’s hypothesis of constants. Neumann and Neumann delivered their investigation of assortments of gatherings, bunches characterized by bunch hypothetical conditions instead of gathering polynomials.
There was additionally a hazardous development in nonstop gatherings in the period 1900-1940. Topological gatherings started to be concentrated on along these lines. There were numerous extraordinary accomplishments in ceaseless gatherings: Container’s characterization of semi-straightforward Falsehood algebras, Weil’s hypothesis of portrayals of conservative gatherings, Haar’s work in the locally smaller case.
Limited bunches filled gigantically in 1900-1940. This period saw the introduction of character hypothesis by Frobenius, Burnside and Schur, which aided answer numerous nineteenth century inquiries in stage gatherings, and opened the way to altogether new methods in conceptual limited gatherings. This period saw Corridor’s work: on the speculation of Sailo’s hypothesis on inconsistent arrangements of primes, which altered the investigation of limited solvent gatherings, and on the power-commutator construction of p-gatherings, including standard p-gatherings and isoclinism. thoughts were incorporated. bunch, which altered the investigation of p-gatherings and was the main significant outcome in this field since the storehouse. This period saw Zassenhaus’ renowned Schur-Zassenhaus hypothesis on the speculation of Lobby’s Storehouse subgroups, as well as his advancement on Frobenius gatherings and the presence of a nearer order of Zassenhaus gatherings.
The profundity, expansiveness and impact of gathering hypothesis became later. The space started to stretch out into regions like arithmetical gatherings, bunch development, and portrayal hypothesis. In a monstrous cooperative exertion in the mid 1950s, bunch scholars prevailed with regards to ordering all limited basic gatherings in 1982 . Finishing and improving on the evidence of characterization are areas of dynamic examination.
Anatoly Maltsev additionally made significant commitments to bunch hypothesis during this time; His initial work was in rationale during the 1930s, however during the 1940s he demonstrated the significant implanting properties of semigroups in gatherings, concentrated on the evenness issue of gathering rings, laid out the Malsev correspondence for polycyclic gatherings, and during the 1960s In the 10 years of the ten years got back to rationale to demonstrate different speculations. Being uncertain inside concentrate on gatherings. Prior, Alfred Tarski demonstrated rudimentary gathering hypothesis to be key.
You may like
Tech
8 Key Reasons To Choose Managed IT Services
Published
2 weeks agoon
July 12, 2024By
danielclarke
Every business, no matter big or small, relies on a robust IT infrastructure. However, navigating the complexities associated with this infrastructure can be challenging, which is why many turn to managed IT services. This approach not only streamlines business operations but also offers countless strategic advantages.
Keep reading this article to learn how these managed IT services can help you take your business to new heights.
1. Enhanced Operational Efficiency
One of the most compelling benefits of managed IT services is enhancing operational efficiency. Businesses can focus on their core competencies by delegating IT responsibilities to a specialised provider. Managed IT services ensure that systems run seamlessly, reducing downtime and increasing productivity. This seamless operation is crucial for maintaining a competitive edge and achieving business goals.
2. Cost Savings with Managed IT Services
Cost efficiency is a significant factor driving the adoption of managed IT services. Traditional in-house IT departments can be expensive, requiring substantial investment in personnel, training, and equipment. Managed IT services, on the other hand, offer a scalable solution that aligns with your budget. Also, predictable monthly costs allow for better financial planning, and the reduced need for capital expenditures can free up resources for other critical areas of your business.
3. Access to Specialised IT Expertise
The role of managed IT service providers is important, as they bring a wealth of knowledge and experience to the table. These providers have teams of certified professionals who stay abreast of the latest industry trends and advancements. This access to specialised IT expertise ensures that your business benefits from cutting-edge solutions and best practices, enhancing overall IT performance and security.
4. Proactive Maintenance and Support
Managed IT services operate on a proactive maintenance model. This means potential issues are identified and resolved before they escalate into major problems. Regular monitoring, updates, and optimisations are part of the package, ensuring your IT infrastructure remains in peak condition. Proactive support not only minimizes downtime but also extends the lifespan of your IT assets, providing long-term value.
5. Robust Security Measures
Managed IT service providers implement comprehensive security protocols to safeguard your data and systems. From firewalls and anti-virus solutions to regular security audits and compliance checks, these providers ensure your business is protected against a wide range of threats. This level of security is especially crucial for small businesses, which may lack the resources to develop and maintain such defences independently.
6. Scalability and Flexibility
Your IT needs keep growing as your business grows. This is why opting for managed IT services becomes important. They offer scalability and flexibility, allowing you to adjust your IT resources in response to changing demands. Whether you are expanding your operations or scaling down, a managed IT service provider can seamlessly accommodate these changes.
7. Disaster Recovery and Business Continuity
Disaster recovery and business continuity are critical components of a resilient IT strategy. Managed IT services typically include comprehensive backup and recovery solutions to protect your data against loss. In the event of a natural or cyber-induced disaster, these services ensure that your business can quickly resume operations with minimal disruption. This preparedness is invaluable in maintaining client trust and minimising financial loss.
8. Strategic IT Planning
Finally, managed IT services contribute to strategic IT planning. By collaborating with a managed IT service provider, businesses can develop a long-term IT roadmap aligning with their objectives. This strategic approach ensures that IT investments are made wisely, supporting business growth and innovation.
Managed IT Services for Small Businesses
Small businesses, particularly, stand to gain significantly from managed IT services. Limited resources and IT budgets can make it challenging to maintain a robust IT infrastructure. Here, managed IT services such as those offered by Managed IT Services Brisbane, prove to be a saviour, as they level the playing field by providing access to enterprise-grade solutions and expertise at an affordable cost. This allows small businesses to compete more effectively in their respective markets.
Managed IT Services Provider Selection Tips
Choosing the right managed IT service provider can be a challenging task. However, to make the task easier, you can follow the below-given tips:
- Assess Your Needs: Understand your specific IT requirements and look for providers that offer tailored solutions.
- Check Credentials: Ensure the provider has relevant certifications and a proven track record.
- Review Security Protocols: Verify that the provider has robust security measures in place to protect your data.
- Consider Scalability: Choose a provider that can scale their services in line with your business growth.
- Read Reviews and Testimonials: Learn from the experiences of other businesses to gauge the provider’s reliability and quality of service.
Conclusion:
Managed IT services offer a strategic approach to handling complex IT demands, providing significant benefits such as cost savings, enhanced security, and improved operational efficiency. By partnering with a managed IT service provider, businesses can focus on their core operations, knowing their IT needs are in capable hands. This partnership not only optimises your business’s IT performance but also ensures sustained growth and success.

Introduction
Spy stock – it sounds intriguing, doesn’t it? The very name conjures up images of secret agents and undercover operations. But in the world of finance, spy stock is something entirely different. So, what exactly is spy stock, and why should you care about it? Understanding spy stock can open up new avenues for investment and financial growth, making it a topic worth exploring.
History of Spy Stock
Origins and Evolution
The concept of spy stock has evolved over time, influenced by technological advancements and market dynamics. Initially, the term was coined to describe stocks that offered unique insights into market trends and investor behavior. Over the years, as financial markets became more complex and interconnected, the importance of spy stock grew, providing investors with valuable information to make informed decisions.
Major Milestones
Key milestones in the history of spy stock include the development of sophisticated analytical tools and platforms that allow investors to track and analyze these stocks in real-time. The rise of big data and machine learning has further revolutionized the field, enabling more accurate predictions and deeper insights.
How Spy Stock Works
Mechanisms Behind Spy Stock
At its core, spy stock involves using specific stocks to gauge market sentiment and predict future trends. These stocks often belong to major companies or industries that have a significant impact on the broader market. By monitoring the performance and trading patterns of these stocks, investors can gain a better understanding of market dynamics.
Key Players Involved
Several key players are involved in the world of spy stock, including financial analysts, institutional investors, and data scientists. These experts use advanced tools and methodologies to analyze spy stock and provide actionable insights to investors.
Types of Spy Stock
Different Categories and Their Features
Spy stocks can be categorized into various types based on their characteristics and the insights they provide. Some common categories include:
- Market Leaders: Stocks of leading companies in various sectors.
- Tech Innovators: Stocks of companies at the forefront of technological advancements.
- Economic Indicators: Stocks that reflect broader economic trends.
Popular Examples
Examples of popular spy stocks include shares of major tech companies like Apple, Google, and Amazon, which are often seen as indicators of technological trends and consumer behavior.
Why Investors Are Interested in Spy Stock
Benefits and Potential Gains
Investors are drawn to spy stock for several reasons. Firstly, these stocks provide valuable insights into market trends, helping investors make more informed decisions. Secondly, they offer the potential for significant gains, especially when identified and leveraged correctly. Finally, spy stocks can serve as a hedge against market volatility, providing a safer investment option in uncertain times.
Case Studies of Successful Investments
Numerous case studies highlight the success of spy stock investments. For example, investors who identified the potential of tech giants like Apple and Amazon early on reaped substantial rewards as these companies grew and dominated their respective markets.
Risks Associated with Spy Stock
Common Pitfalls and Dangers
However, investing in spy stock is not without risks. Common pitfalls include over-reliance on a single stock or sector, misinterpretation of market signals, and failure to diversify. Additionally, the volatile nature of financial markets means that even the most well-researched investments can sometimes go awry.
How to Mitigate Risks
To mitigate these risks, investors should adopt a diversified investment strategy, continuously monitor market trends, and remain flexible in their approach. Utilizing stop-loss orders and other risk management tools can also help protect investments.
How to Invest in Spy Stock
Step-by-Step Guide
Investing in spy stock involves several steps:
- Research: Identify potential spy stocks based on market influence and historical performance.
- Analysis: Use analytical tools to assess the stocks’ performance and potential.
- Strategy: Develop a clear investment strategy, including entry and exit points.
- Execution: Invest in the chosen stocks, monitoring their performance regularly.
- Review: Continuously review and adjust the investment strategy based on market changes.
Important Considerations for Beginners
For beginners, it’s crucial to start with a small investment and gradually increase exposure as you gain more experience and confidence. Consulting with financial advisors and using demo accounts to practice trading can also be beneficial.
Tools and Resources for Spy Stock Analysis
Software and Platforms
Several software and platforms are available to help investors analyze spy stock. Popular options include Bloomberg Terminal, Reuters Eikon, and various online trading platforms that offer real-time data and advanced analytical tools.
Essential Metrics and Indicators
Key metrics and indicators to consider when analyzing spy stock include:
- Price-to-Earnings (P/E) Ratio: Measures the stock’s valuation.
- Earnings Per Share (EPS): Indicates the company’s profitability.
- Moving Averages: Helps identify trends and potential entry/exit points.
Spy Stock vs. Traditional Stocks
Key Differences and Similarities
While spy stocks and traditional stocks share some similarities, there are key differences. Spy stocks are typically chosen for their ability to provide market insights, whereas traditional stocks are often selected based on individual company performance. Additionally, spy stocks tend to be more closely monitored and analyzed, making them a more data-driven investment choice.
Pros and Cons of Each
Pros of spy stocks include better market insights and potential for high returns. However, they can be riskier due to their reliance on market trends. Traditional stocks, on the other hand, offer more stability and long-term growth potential but may not provide the same level of insight or rapid gains.
Market Trends and Future Predictions
Current Trends Shaping the Market
Current trends in the spy stock market include increased use of artificial intelligence and machine learning for analysis, greater emphasis on environmental, social, and governance (ESG) factors, and the growing influence of retail investors through platforms like Robinhood.
Expert Predictions for the Future
Experts predict that the importance of spy stock will continue to grow as markets become more complex and data-driven. Innovations in technology and analytics are expected to provide even deeper insights, making spy stock an essential tool for savvy investors.
Regulations and Legal Considerations
Legal Framework Governing Spy Stock
The legal framework for spy stock is similar to that of traditional stock trading, with regulations set by bodies like the Securities and Exchange Commission (SEC) in the United States. These regulations ensure transparency, fairness, and accountability in the market.
Compliance and Ethical Issues
Investors must be aware of compliance and ethical issues, such as insider trading and market manipulation. Adhering to legal guidelines and maintaining ethical standards is crucial for long-term success in spy stock trading.
Notable Figures in the Spy Stock Industry
Influential People and Their Contributions
Several notable figures have made significant contributions to the spy stock industry. Investors like Warren Buffett and Peter Lynch have popularized the use of specific stocks to gain market insights, while tech innovators like Elon Musk have influenced market trends through their companies.
Lessons from Their Success
The success of these figures teaches us the importance of thorough research, disciplined investment strategies, and staying ahead of market trends. Their approaches to spy stock can serve as valuable lessons for aspiring investors.
Case Studies of Spy Stock
In-depth Analysis of Noteworthy Cases
Examining case studies of spy stock investments can provide valuable insights. For example, the rapid rise of Tesla’s stock in recent years highlighted the growing influence of electric vehicles and renewable energy, offering a blueprint for identifying future market trends.
What We Can Learn from Them
These case studies teach us the importance of identifying emerging trends early, diversifying investments, and remaining adaptable in the face of market changes. They also emphasize the value of continuous learning and staying informed about industry developments.
Tips for Successful Spy Stock Trading
Expert Advice and Best Practices
Experts recommend several best practices for successful spy stock trading, including:
- Stay Informed: Regularly update yourself on market news and trends.
- Use Advanced Tools: Leverage technology and analytical tools for better insights.
- Diversify: Spread your investments across different sectors to minimize risk.
- Monitor Performance: Continuously track the performance of your investments and adjust strategies as needed.
Common Mistakes to Avoid
Common mistakes to avoid in spy stock trading include:
- Overconfidence: Believing you can predict the market with certainty.
- Neglecting Research: Failing to thoroughly research and analyze potential investments.
- Ignoring Risks: Underestimating the risks associated with spy stock trading.
Conclusion
In conclusion, spy stock offers a fascinating and potentially lucrative avenue for investors. By understanding its history, mechanisms, and the various factors influencing its performance, you can make more informed decisions and enhance your investment strategy. Whether you’re a seasoned investor or a beginner, spy stock provides valuable insights into market trends and opportunities for growth.
FAQs
What is Spy Stock? Spy stock refers to specific stocks used to gauge market sentiment and predict future trends. These stocks often belong to major companies or industries that significantly impact the broader market.
How can I start investing in Spy Stock? To start investing in spy stock, begin with thorough research, use analytical tools to assess potential stocks, develop a clear investment strategy, and continuously monitor and adjust your investments.
What are the risks of Spy Stock? Risks include over-reliance on a single stock or sector, misinterpretation of market signals, and market volatility. Diversification and continuous monitoring can help mitigate these risks.
Are there any legal issues with Spy Stock? The legal framework for spy stock is similar to traditional stock trading, with regulations ensuring transparency and fairness. Investors must also adhere to ethical standards to avoid issues like insider trading.
What resources can help me understand Spy Stock better? Resources include financial news platforms, analytical tools like Bloomberg Terminal and Reuters Eikon, and educational materials from reputable financial institutions.
Tech
Snapchat Planets: A Comprehensive Guide to Understanding the Solar System of Your Friends
Published
2 months agoon
May 29, 2024By
admin
Introduction
Ever wondered how Snapchat decides who your closest friends are? Enter the world of Snapchat Planets, a unique feature that visualizes your social interactions in a fun and engaging way. This guide will take you on a journey through the solar system of your Snapchat friends, explaining everything you need to know about this intriguing feature.
The Concept Behind Snapchat Planets
Snapchat Planets originated from the idea of gamifying social interactions. By representing friends as planets in a solar system, Snapchat adds a playful twist to understanding your social connections. This feature not only makes it easy to see who you interact with the most but also adds a visual element to your friend dynamics.
Understanding Your Snapchat Solar System
The Basics of Snapchat Solar System
Your Snapchat Solar System is a visual representation of your closest friends, depicted as planets orbiting around you (the sun). Each planet represents a different level of interaction, with those closest to the sun being your most interacted friends.
How to Access Your Snapchat Solar System
To access your Snapchat Solar System, navigate to the Friends page. Here, you’ll find the Bitmoji of your friends arranged in a solar system format. The closer the planet is to the center, the more frequent and meaningful your interactions are with that friend.
The Planets and Their Meanings
Mercury: The Closest Friends
Mercury, the closest planet to the sun, symbolizes your top friend on Snapchat. This is the person you snap and chat with the most.
Venus: The Second-Closest Friends
Next is Venus, representing friends who are almost as close as Mercury but not quite there. These are people you interact with very frequently.
Earth: Friends You Interact with Regularly
Earth signifies friends you have regular interactions with. They are not your top friends but still hold significant space in your social circle.
Mars: Friends You Occasionally Interact With
Mars represents friends you communicate with occasionally. These are not your go-to friends but still part of your social interactions.
Jupiter: Friends You Rarely Interact With
Jupiter is for friends you rarely interact with. They are on your friend list but don’t frequently communicate with you.
Saturn: Friends with Similar Interests
Saturn signifies friends with whom you share common interests. These friends may not be the closest, but you bond over shared hobbies or topics.
Uranus: Friends with Mutual Connections
Uranus represents friends who are part of your extended network through mutual connections. You might not interact directly often, but you share many common friends.
Neptune: Friends You Seldom Communicate With
Neptune, being the farthest, symbolizes friends you barely communicate with. These friends are at the edge of your social circle.
The Algorithm Behind Snapchat Planets
How Snapchat Determines Planet Positions
Snapchat uses a combination of interaction frequency, chat duration, snap exchanges, and mutual connections to determine the positions of friends in your solar system.
Factors Influencing Planetary Positions
Factors like the number of snaps exchanged, chat frequency, and story interactions play crucial roles in determining who appears where in your Snapchat Solar System.
Benefits of Snapchat Planets
Enhancing Social Connections
Snapchat Planets help you understand your social connections better, making it easier to identify who your closest friends are and who you might need to engage with more.
Understanding Your Social Circles
This feature provides insights into your social behavior, helping you understand the dynamics of your friend circle and encouraging you to maintain or strengthen relationships.
How to Improve Your Planetary Status
Tips for Becoming a ‘Closer’ Friend
Engage more with friends you want to bring closer in your Snapchat Solar System. Send more snaps, engage in longer chats, and interact with their stories.
Engaging More on Snapchat
Consistent interaction is key. Regularly check in with friends, respond to their snaps and stories, and keep the conversation going.
Common Misconceptions About Snapchat Planets
Debunking Myths
One common myth is that Snapchat Planets are publicly visible. In reality, they are only visible to you, ensuring privacy in your social interactions.
Clarifying Misunderstandings
Another misunderstanding is that the positions are permanent. In fact, they change based on your interactions, allowing for dynamic social representation.
Snapchat Planets and Privacy Concerns
How Snapchat Protects Your Privacy
Snapchat ensures that your solar system data is private and not shared with others. Only you can see the arrangement of your friends.
Managing Your Snapchat Solar System Settings
You can manage your settings to control who appears in your solar system and adjust privacy settings to suit your comfort level.
The Future of Snapchat Planets
Potential Updates
Snapchat is continuously evolving. Future updates may include more interactive elements or personalized features based on user feedback.
User Feedback and Potential Improvements
Users have suggested various improvements, such as adding more planets or providing insights into why friends are positioned where they are. Snapchat is likely to consider these suggestions for future updates.
User Experiences with Snapchat Planets
Testimonials and Stories
Many users enjoy the visual representation of their social interactions. For instance, one user mentioned how they realized they had drifted apart from a close friend and made efforts to reconnect.
Real-Life Examples
Another user shared how seeing a friend move from Mars to Venus in their solar system encouraged them to strengthen that friendship, leading to a closer bond.
Snapchat Planets vs. Other Social Media Features
Comparing to Facebook Friends Lists
Unlike Facebook’s static friends list, Snapchat Planets offer a dynamic and interactive way to view social connections, making it more engaging.
Comparing to Instagram Close Friends
While Instagram’s close friends feature is more about sharing content selectively, Snapchat Planets focus on interaction levels, providing a different perspective on social connections.
The Role of Snapchat Planets in Marketing
How Brands Use Snapchat Planets
Brands leverage Snapchat Planets to identify key influencers and engage with their most interactive followers, enhancing their marketing strategies.
Case Studies of Successful Campaigns
Several brands have successfully used Snapchat Planets to create personalized marketing campaigns, resulting in higher engagement and brand loyalty.
Challenges of Snapchat Planets
Navigating the Complexity
Understanding the dynamic nature of Snapchat Planets can be challenging, especially for new users. It requires regular engagement to keep up with changes.
User Adaptation
Some users may find it hard to adapt to this feature initially, but with time, they often find it a valuable addition to their social media experience.
Conclusion
Snapchat Planets provide a fascinating glimpse into your social world, helping you understand and enhance your connections. By visualizing your friend interactions, Snapchat makes it easier to see who matters most in your social universe. As you explore this feature, you’ll likely find new ways to engage and strengthen your friendships.
FAQs
What are Snapchat Planets? Snapchat Planets is a feature that visualizes your friends as planets in a solar system, representing your levels of interaction with them.
How do I see my Snapchat Planets? You can see your Snapchat Planets by going to the Friends page on Snapchat, where your friends are displayed as planets in a solar system format.
Can I change the position of friends in my Snapchat Solar System? No, the positions are determined by your interaction patterns, but you can influence these by increasing or decreasing your interactions with friends.
Are Snapchat Planets visible to others? No, Snapchat Planets are only visible to you, ensuring your privacy.
What if I don’t want to be in someone’s Snapchat Solar System? You can manage your privacy settings and interactions to influence your presence in others’ Snapchat Solar Systems.

India National Cricket Team vs South Africa National Cricket Team Match Scorecard: A Detailed Analysis

8 Key Reasons To Choose Managed IT Services

The Irresistible Rise of Pizza Edition Games: A Delicious Journey through Gaming

Get your Canadian visa in a jiffy – Hong Kong citizens can now apply online!
BiharMasti: The Place to Download Bhojpuri Movies and Music

What states have no chase law for motorcycles
Trending
-

 Business2 years ago
Business2 years agoGet your Canadian visa in a jiffy – Hong Kong citizens can now apply online!
-
 Tips & Tricks2 years ago
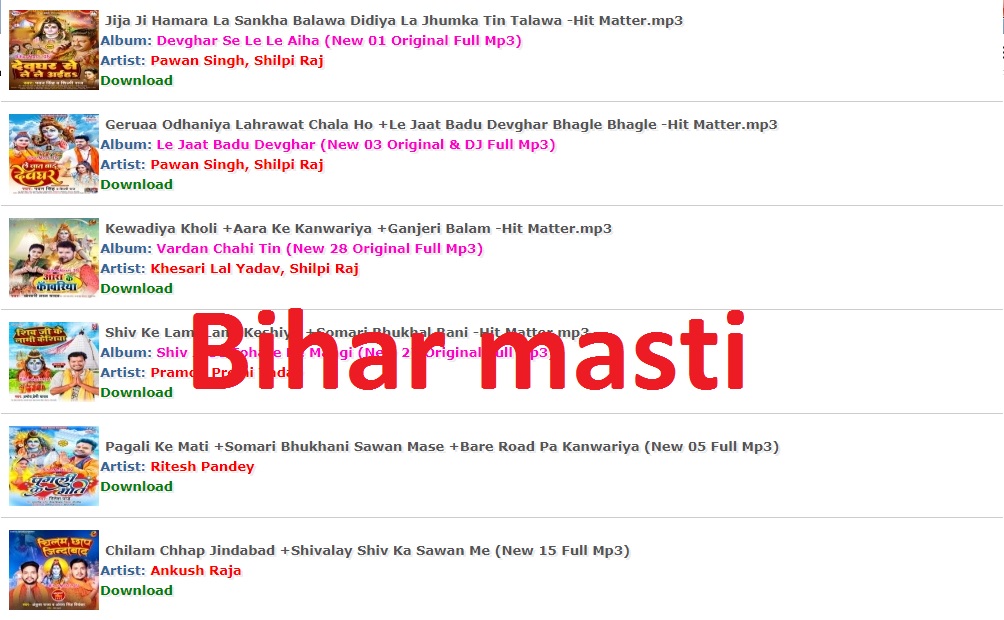
Tips & Tricks2 years agoBiharMasti: The Place to Download Bhojpuri Movies and Music
-

 Law2 years ago
Law2 years agoWhat states have no chase law for motorcycles
-

 Technology2 years ago
Technology2 years agoHow to do Jio Prepaid Recharge Online
-

 Business2 years ago
Business2 years agoHow do MEP Services help contractors?
-

 Business1 year ago
Business1 year agoEverything You Need to Know About SQM Club
-

 Lifestyle2 years ago
Lifestyle2 years agoWhat is a lifestyle party? Few tips for hosting a lifestyle party
-
 Technology2 years ago
Technology2 years agoHow to Download Punjabi Movie Chhalla Mud Ke Nahi Aaya?

